Dictators subvert the police and justice system. They coerce tech firms and cell providers to share information about private messages. How can you communicate securely in such a hostile environment?
Mark Zuckerberg's Meta donates $1m to Trump fund - BBC
Pregnant Women Sharing Pregnancy-Related Information on Facebook - PMC
Facebook is reportedly letting anti-abortion activists target ads at people seeking abortions - MIC
How women's phones became a tool for abortion surveillance - MSNBC
How ICE Uses Social Media to Surveil and Arrest Immigrants - The Intercept
Elon Musk Tells Followers to Use Signal Messaging App - PC Mag
Protect your communication with MakeItPrivate.org, a free service that you can use online or without connectivity. You can even encrypt and decrypt messages on your phone without cell coverage. Print out messages and mail through the U.S. Postal Service. Print a QR code and post it on social media where only people with whom you've shared a secret password can read.
How you're tracked
Your phone and laptop give away your location with IPlocation.net. Click here to see your current location.
Google scans your emails.
Facebook and Instagram are known for tracking your online behavior.
Here’s what an eavesdropper sees when you use an unsecured Wi-Fi hotspot. - PC World
Chinese hackers gained access to huge trove of Americans’ cell records - Politico
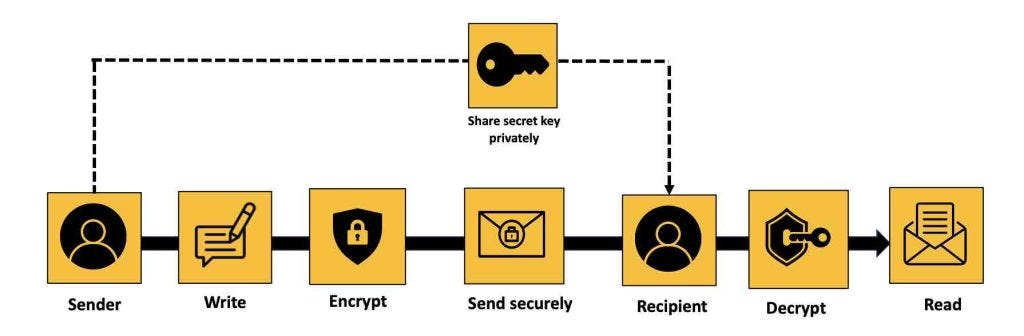
How Make It Private works
Make It Private is a free service that you can use anonymously from a phone of laptop, without having to register yourself or downloading an app. You can even use Make It Private without internet connectivity to encrypt and decrypt messages. Encrypted messages can be sent as a text or a QR Code.
Encrypt your message before sharing it through Google Mail, Facebook, SMS, or other messaging platform. This helps ensure that even if someone is monitoring your messages it is much harder for them to read it because the message is encrypted. You can also decide to print the encrypted message or the QR Code (as in the image above). Scanning the QR Code places the encrypted message into the INPUT BOX of Make It Private. Enter the SECRET KEYWORD to decrypt and read the message.
Understand the danger
"Adversaries are Nation-State-level law enforcement, or local law enforcement with some access to Nation-State-level law enforcement resources. Despite end-to-end encryption hiding the contents of messages in transit, these adversaries have many capabilities which could be used to uncover or disrupt activities, communications, or networks so they can repress people." - PET Guide
How adversaries are tracking you
They have trivial access to social media sites and other public information.
In some cases, they can monitor all home or cell phone internet traffic for a specific targeted individual.
They can access “anonymized” user data or metadata from apps, cell phone providers, isps, etc.
They can access recorded network traffic collected en masse from many bottlenecks in internet infrastructure.
To varying degrees of success they can combine, analyze, and correlate such data and network traffic in order to de-anonymize users, map social networks, or reveal other potentially incriminating information about individuals or groups and their communications.
They can compromise internet infrastructure (ISPs, service providers, corporations, app developers) either through coercion or hacking.
They can disrupt internet traffic in general or in targeted ways, either because they control internet infrastructure, or by wielding cyberattacks against internet infrastructure.
Elon Musk wants you to use Signal !
Final word
"This entire discussion has been about secure communication chat apps that run on our phones and computers. The final word must be a reminder that as much as using tools that encrypt and anonymize online communications can empower you and protect you against adversaries, you should still never type or say anything into any app or device without appreciating it could be read back to you in court. Meeting with your friends, face-to-face, outdoors and away from cameras and other electronics is by far the safest way to have any conversation that needs to be secure and private. Turn off your phone, put it down, and go outside!" - PET Guide
Take Away: Protect your privacy. Communicate securely. Use MakeItPrivate.org online or without an internet connection.
Deepak
DemLabs
DISCLAIMER: ALTHOUGH THE DATA FOUND IN THIS BLOG AND INFOGRAPHIC HAS BEEN PRODUCED AND PROCESSED FROM SOURCES BELIEVED TO BE RELIABLE, NO WARRANTY EXPRESSED OR IMPLIED CAN BE MADE REGARDING THE ACCURACY, COMPLETENESS, LEGALITY OR RELIABILITY OF ANY SUCH INFORMATION. THIS DISCLAIMER APPLIES TO ANY USES OF THE INFORMATION WHETHER ISOLATED OR AGGREGATE USES THEREOF.








Me too. But it's always better to be cautious.
We're coming out with a version this week which can run offline without having to connect to the internet. That will let people use it offline and share the solution with others using Bluetooth which will help get it into more hands discreetly.
"Any text protected by a keyword can be decrypted without the keyword, I believe." - Not easily without a lot of processing power. Read more:
"Strong Cryptography refers to the use of robust encryption techniques, such as AES or Triple DES, to protect sensitive data from unauthorized access. It involves storing data in a secure manner, either by hashing or symmetric encryption, to prevent data breaches and ensure data confidentiality." - https://www.sciencedirect.com/topics/computer-science/strong-cryptography
The attacker must go through the time-consuming exercise of cracking password hashes to obtain the actual credentials. Another clear benefit to hashing is that it eliminates the key management issues associated with encryption. To stay consistent with security best practices, ensure that the hashing algorithm of choice has not been determined mathematically susceptible to collisions, such as MD5 and SHA-1. Consult resources such as NIST (http://csrc.nist.gov/groups/ST/hash/policy.html) to find out the current set of hashing algorithms deemed acceptable for use by federal agencies.